1. What is a Transactional Processing and the role of TP systems. State the key objective of TP/TPSs.
1. What is a Transactional Processing and the role of TP systems. State the key objective of TP/TPSs. Transaction processing (TPSs) monitor, collect, store, and process data generated from all business transactions. These data are inputs to the organization’s database. TPSs have to handle high volume and large variations in volume efficiently, avoid errors and downtime, record results accurately and securely, and maintain privacy and security. The backbone of most information systems applications is the transaction processing system.
Section 8.2 - 1. What is a functional area information system? List its major characteristics. Functional area information systems (FAISs) provide information mainly to lower and middle-level managers in the functional areas. They use this information to help them plan, organize, and control operations. The information is provided in a variety of reports (routine, ad hoc and exception) and provide information to managers regardless of their functional areas. Routine reports are produced at scheduled intervals. Ad-hoc reports also can include requests for drill-down reports, key-indicator reports and comparative reports. And exception reports include information that falls outside certain threshold standards.
2. How does an FAIS support management by exception? How does it support on-demand reports? Exception reports include information that falls outside certain threshold standards. Ti implement management by exception, management first creates performance standards. The company then sets up systems to monitor performance, compare actual performance to the standards, and identify predefined exceptions. Managers are alerted to the exceptions via exception reports.
On-demand reports, which are non-routine reports are supported in these ways and through these types:
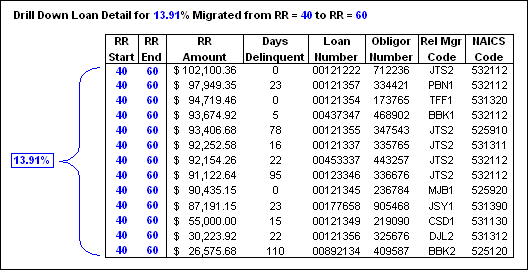
- Drill-down reports show a greater level of detail. For example, a manager might examine sales by region and decide to “drill down to more detail” to look at sales by store and then by salesperson.
- Key-indicator reports summarize the performance of critical activities. For example, a chief financial officer might want to monitor cash flow and cash on hand.
- Comparative reports compare. For example, the performances of different business units or time periods.
 Section 8.3 1. Define ERP and describe its functionalities.
Section 8.3 1. Define ERP and describe its functionalities. Enterprise resource planning (ERP) systems integrate the planning, management, and use of all of an organization’s resources. The major objectives of ERP systems are to tightly integrate the functional areas of the organization and to enable information to flow seamlessly across the functional areas. ERP systems provide the information necessary to control the business processes of the organization. ERP software includes a set of interdependent software modules, linked to a common database, that provide support for the internal business processes in the following functional areas: finance and accounting, sales and marketing, manufacturing and production, and human resources.
2. List some drawbacks of ERP software. ERP systems can be extremely complex, expensive, and time consuming to implement. Companies may also need to change existing business processes to fit the predefined business processes of the software. Finally, companies must purchase the entire software package even if they require only a few of the modules.
Section 8.5 1. Define a supply chain and supply chain management (SCM). A supply chain refers to the flow of materials, information, money and services from raw material suppliers, through factories and warehouses to the end customers. A supply chain also includes the organizations and processes that create and deliver products, information, and services to end customers.
Supply chain management’s (SCM) function is to plan, organize, and optimize the supply chain’s activities. The goal of SCM systems is to reduce friction along the supply chain. Friction can involve increased time, costs, and inventories as well as decreased satisfaction.
 2. List the major components of supply chains.
2. List the major components of supply chains. The supply chain involves three segments or components:
1. Upstream: where sourcing or procurement from external suppliers occurs (orders, information, payments, returns)
2. Internal, where packaging, assembly, or manufacturing takes place.
3. Downstream, where distribution takes place, frequently by external distributors (products, services, information)
3. What is the bullwhip effect? The bullwhip effect refers to erratic shifts in orders up and down the supply chain. Basically, customer demand variables can become magnified when they are viewed through the eyes of managers at each link in the supply chain.
Section 8.6 1. Define EDI and list its major benefits and limitationsElectronic Data Interchange (EDI) is a communication standard that enables business partners to exchange routine documents, such as purchasing orders, electronically. EDI formats these documents according to agreed-upon standards and then transmits messages using a converter, called a translator.
Benefits - Minimizes data entry errors because each entry is checked by the computer.
- The length of the message can be shorter, and the messages are secured.
- Reduces cycle time.
- Increases productivity.
- Enhances customer service.
- Minimizes paper usage and storage.
Limitations - Implementing an EDI system involves a significant initial investment.
- The ongoing operating costs also are high, due to the use of expensive, private VANs.
- The traditional EDI system is inflexible.
- Many EDI standards are in use today. As a result, one company might have to use several standards in order to communicate with different business partners.